Kubernetes GitOps with FluxCD - Part 5 - Implementing Discord Alerts
Table of Contents
In previous post, we explored how to setup helm chart automation with FluxCD, Building on our foundation of basic Flux CD setup, SOPS-based secret management, image update automation and Helm Chart Automation, this article focuses on implementing FluxCD Alerts with Discord integration to enhance GitOps observability stack.
Alerts provide real-time notifications about the state of our GitOps operations, helping us respond promptly to issues and stay informed about successful reconciliations. Let’s dive into configuring in our Kubernetes cluster.
1. Obtaining the Discord Webhook URL
First, we need to acquire a Webhook URL from Discord:
- Navigate to your Discord server settings
- Select “Integrations”
- Click on “Webhooks”
- Create a new webhook or use an existing one
- Copy the generated webhook URL
2. Securely Store the Webhook URL
Next, we’ll securely store the webhook URL as a Kubernetes secret by creating cluster/default/discord-webhook-secret.yaml:
1apiVersion: v1
2kind: Secret
3metadata:
4 name: discord-webhook-secret
5 namespace: flux-system
6type: Opaque
7stringData:
8 address: https://discordapp.com/api/webhooks/XXXXXX/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Following our established security practices, we’ll encrypt this sensitive information with SOPS and commit the changes to our Git repository as detailed in our SOPS-based secret management post.
3. Configuring Alert Resources
With our webhook secured, we can now configure the alert resources. Create cluster/default/discord-alert.yaml with the following content:
1apiVersion: notification.toolkit.fluxcd.io/v1beta3
2kind: Provider
3metadata:
4 name: discord
5 namespace: flux-system
6spec:
7 type: discord
8 secretRef:
9 name: discord-webhook-secret
10---
11apiVersion: notification.toolkit.fluxcd.io/v1beta3
12kind: Alert
13metadata:
14 name: discord-info-alert
15 namespace: flux-system
16spec:
17 eventMetadata:
18 cluster: "default"
19 providerRef:
20 name: discord
21 eventSeverity: info
22 eventSources:
23 - kind: GitRepository
24 name: '*'
25 - kind: Kustomization
26 name: '*'
27 - kind: HelmRelease
28 name: '*'
29 - kind: ImageUpdateAutomation
30 name: '*'
This configuration creates two resources:
- A
Providerthat specifies Discord as our notification destination - An
Alertthat defines which events should trigger notifications
As of the time of writing, FluxCD supports the following event sources (as referenced at https://pkg.go.dev/github.com/fluxcd/notification-controller/api/v1#CrossNamespaceObjectReference )
- Bucket
- GitRepository
- Kustomization
- HelmRelease
- HelmChart
- HelmRepository
- ImageRepository
- ImagePolicy
- ImageUpdateAutomation
- OCIRepository
4. Verifying the Configuration
After committing these changes to Git and allowing FluxCD to reconcile them, let’s verify that our alerts are properly configured:
1flux get alerts
2
3NAME SUSPENDED READY MESSAGE
4discord-info-alert False True Alert is Ready
The READY status confirms that our alert configuration has been successfully applied.
5. Testing the Alert System
To validate that our alerts are functioning as expected, let’s trigger an event by removing a previously created resource. In this case, we’ll delete the nginx deployment we created during our initial FluxCD setup.
1rm cluster/default/nginx.yaml
After committing and pushing this change, we should observe a notification in our Discord channel:
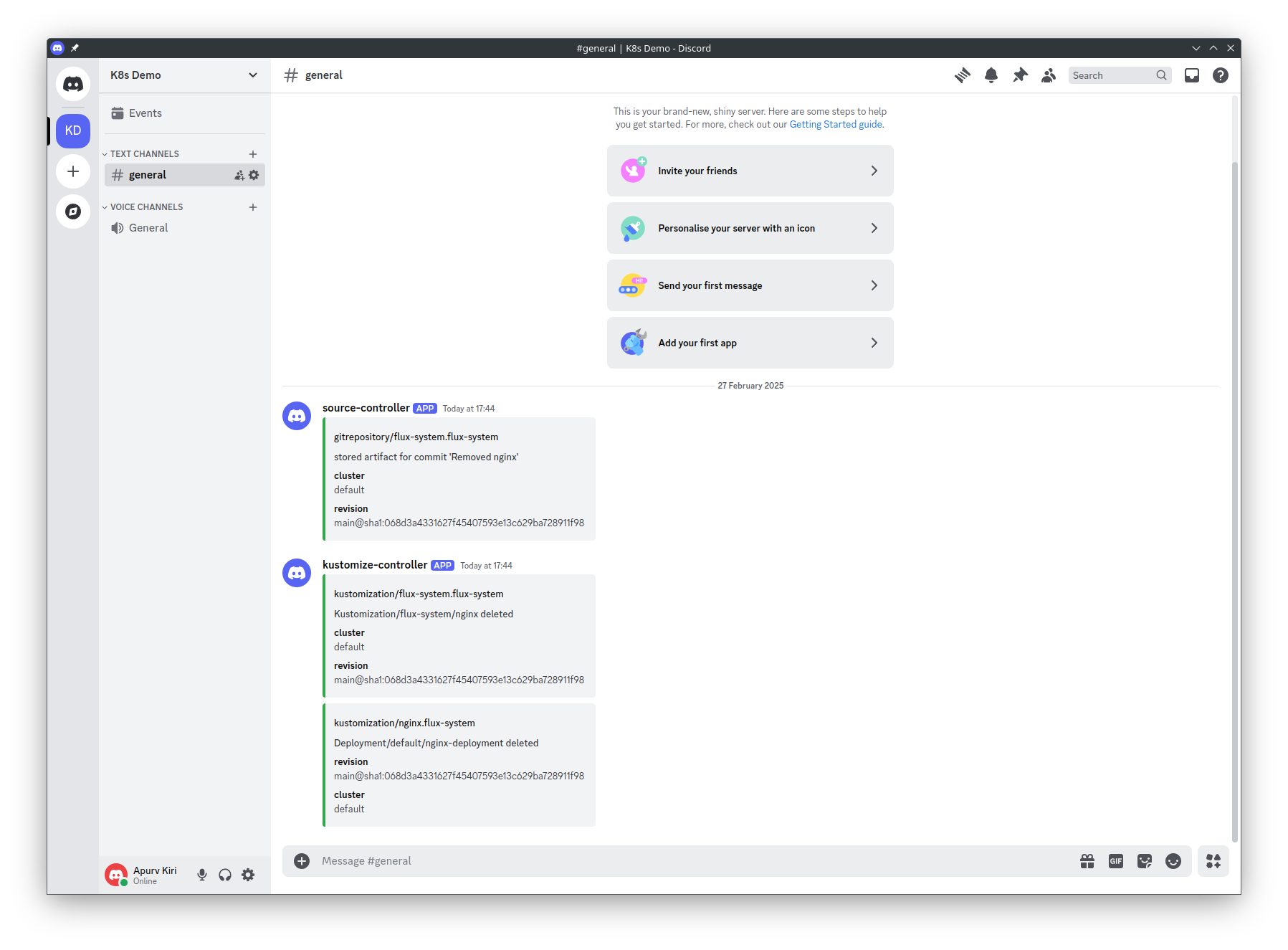
Success! We have received the notification, confirming that our alert system is operational and correctly integrated with Discord.
Best Practices for FluxCD Alerts
When implementing alerts in your GitOps workflow, consider these best practices:
- Filter by Severity: Configure different alerts for various severity levels (info, error, warning) to avoid alert fatigue
- Use Namespaces: Organize alerts by namespace to better manage notifications in larger clusters
- Integration Options: Beyond Discord, consider integrating with other platforms like Slack, Microsoft Teams, or PagerDuty for comprehensive coverage
- Alert Routing: Route critical alerts to urgent channels and informational alerts elsewhere
What next ?
In forthcoming articles, we’ll explore more advanced GitOps patterns with FluxCD, including:
- Push based reconciliation triggers with Webhook receivers
Stay tuned for each of these topics.
References
- Official FluxCD Documentation - https://fluxcd.io/flux/monitoring/alerts/
- GitOps Working Group - https://opengitops.dev
- Kubernetes Documentation - https://kubernetes.io/docs/
- FluxCD Notification Controller API - https://pkg.go.dev/github.com/fluxcd/notification-controller/api/v1
- Discord Webhook Documentation - https://discord.com/developers/docs/resources/webhook